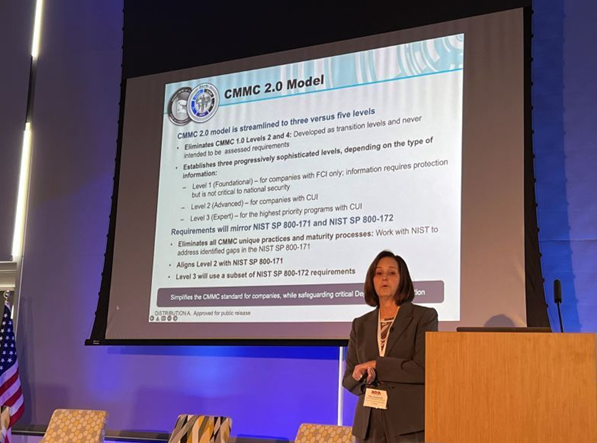
On April 7th, Direct iT attended the NDIA’s informative session on Zero Trust and CMMC 2.0 at Northeastern University’s Innovation Campus in Burlington, MA. Many people deeply involved in CMMC 2.0 traveled from all around the country to participate, including Stacy Bostjanick, head of the CMMC program in the Office of the DoD CIO, who gave a fascinating talk.
Bostjanick entertained some lively questions from the audience that seemed to point towards CMMC 2.0 level 2 being the requirement on the vast majority of contracts, with CMMC 2.0 level 1 and CMMC 2.0 level 2 Advanced both being in the minority of contracts (if used at all).
Bostjanick also gave a few optimistic unofficial guesses about the timeline and rollout of the CMMC 2.0 process (although Direct iT’s guess is that it seems actual pre-contract-award CMMC 2.0 audits for the entire DiB supply chain are still years away).
However, all of the presenters agreed that NIST 800-171 requirements are still in place on all current DoD contracts that handle CUI via the 252 204-7019 clause. These NIST 800-171 requirements essentially haven’t changed since they were first introduced in 2014 (it’s the same 110 required controls).
There also was discussion of the CMMC 2.0 scoping guide recently released by the DoD. This guide, while clarifying some details of how CMMC 2.0 applies to common cloud services and MSPs, unfortunately, left many more questions unanswered.
Particularly, while the guide did lay the foundation for responsibility matrices and categories for different types of external services, it did not clarify exactly which in-scope CMMC 2.0 practices are applicable to common situations (such as EDR platforms, RMM tools, SIEM tools, and MSSPs).
DIT’s Top 5 5 CMMC 2.0 “Gotchas” and Common Misconceptions
- NIST 800-171’s 110 controls refer to NIST 800-171A (which is a separate document)’s assessment objectives– if you are not meeting every assessment objective you fail that control - many controls may have 5 or 6 assessment objectives and you need all 320 assessment objectives met in order for all 110 controls to be in place.
- NIST 800-171’s appendices also point to the 61 NFO controls, a set of basic security policies that the creators of NIST 800-171 assumed all organizations seeking certification would already have in place- these controls are taken from NIST SP800-53
- Requirements flow down to External Service Providers (including cloud service providers and MSPs) and to Security Protection Assets (including SIEM providers, EDR providers, RMM providers) according to the CMMC 2.0 level 2 scoping guide released in December 2021.
- The same scoping guide said that all when an External Service Provider is used, there should be a Responsibility Matrix outlining which CMMC practices the External Service Provider is involved in
- Requirements are in contracts now (and the DOJ’s Cyber-Fraud Initiative recently collected a $930,000 settlement from a federal contractor where a data breach revealed contractual cybersecurity requirements were unmet).



You must be logged in to post a comment.